Buddy’s main projects
Fitting it all in
Managing new construction
Buddy Hickman, EVP/CIO, Albany Medical Center, Discusses His CHIME Survey on HIPAA And IT Security, Chapter 2
Buddy Hickman, EVP/CIO, Albany Medical Center, Discusses His CHIME Survey on HIPAA And IT Security, Chapter 1
CHIME Wants Reduced Reporting Burden In Proposed HIPAA Changes
Proposed HIPAA changes establish standards that would be difficult for providers to meet and should be scaled back, according to comments filed by CHIME. The organization said the rules rely too much on technical capabilities that are not widely available and fail to acknowledge the amount of human intervention that will be necessary to achieve […]
Is Your HIE Taking Privacy Seriously Enough?
In late June, it was reported that the Rhode Island affiliate of the American Civil Liberties Union (ACLU) was bringing suit against the Rhode Island Department of Health, claiming that the rules adopted by DOH to establish a statewide HIE do not go far enough, nor are they explicit enough, to protect patient privacy. In its suit, the ACLU asks the Rhode Island State Superior Court to declare the rules made public by the DOH “incomplete and not compliant with HIE requirements.”
Privacy & Security Tiger Team Hunts Balance
The HIT Policy Committee’s new Privacy and Security Tiger Team workgroup is striving to establish the requirements that intermediaries in personal health information (PHI) message transactions will be subject to. Under HIPAA, parties which have access to PHI are deemed covered entities (CEs), required to establish business associate agreements (BAAs) which obligate them to handle the data in certain ways. With the rise of health information exchange under the HITECH Act, the Office of the National Coordinator created the Tiger Team to provide it with guidance in governing health information organizations (HIOs) — or third-party intermediaries which have varying degrees of involvement with the messages.
Data Security – Pay Now or Pay (More) Later
As we enter the era of Meaningful Use, we are truly seeing an increased realization of the central role that IT plays in provider strategic planning. Happily, we are also starting see recognition from many corners of healthcare organizations of the wisdom of making targeted, shrewd, IT investments as down payments on organizations’ futures. And […]
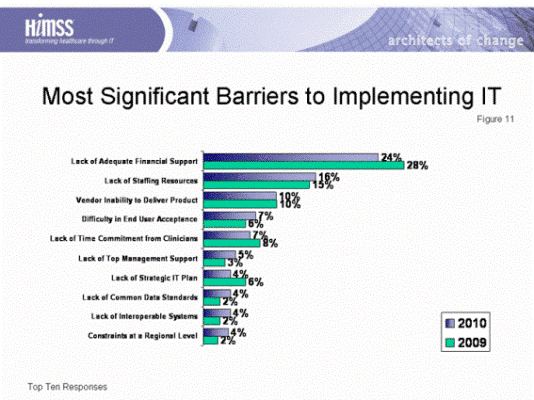
HIMSS Survey Shows Security a Dark Cloud
Other than a major focus on Meaningful Use and clinical systems, security concerns are a top priority, with one third of respondents (34 percent) saying an internal breach was their top worry in that area, and nearly one-quarter (23 percent) said their organization had a security breach in the past year, according to 21st Annual […]
One-on-One w/KLAS Clinical GM Jason Hess (III)
Before the term HIE appeared in the pages of HITECH, many CIOs didn’t pay it much attention, preferring instead to focus on getting their houses in order. While that’s still a great strategy, healthcare informatics leaders now have no choice but to dip their toes into the murky waters of inter-organizational information exchange. While many […]